Blog
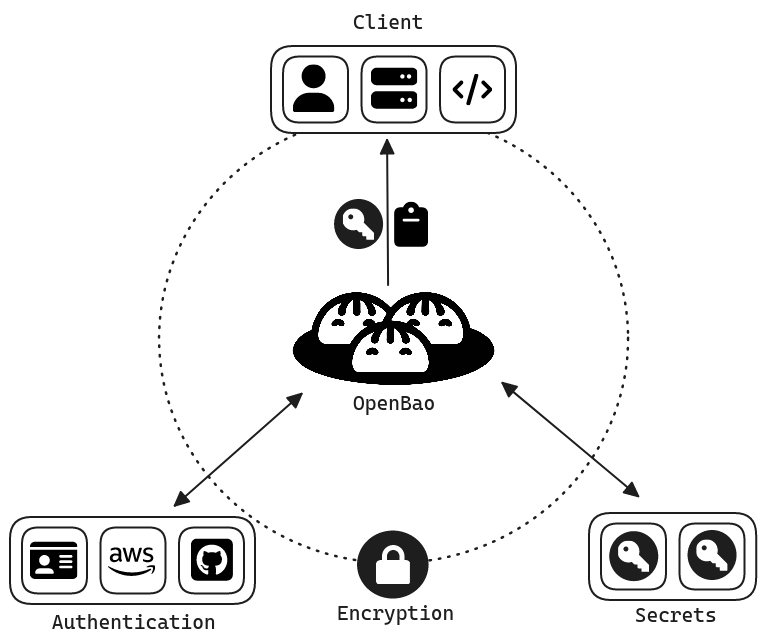
OpenBao: Wahrung der Zukunft des Open-Source-Secrets-Management
In der komplexen Technologielandschaft von heute ist die Verwaltung von Secrets wie API-Schlüsseln, Passwörtern, Zertifikaten und anderen sensiblen Daten, zu einer der größten Herausforderungen für Unternehmen geworden. Aus diesem Grund unterstützt Liquid Reply OpenBao, ein Open-Source-System zur Verwaltung von Secrets und Verschlüsselung auf Identitätsbasis, um die Datenverwaltung im Cloud-Zeitalter zu sichern.
Solving Kubernetes Multi-tenancy Challenges with vCluster
Erfahren Sie, wie vCluster die Einschränkungen der Mandantenfähigkeit von Kubernetes für interne Entwicklerplattformen durch die Erstellung isolierter virtueller Cluster innerhalb von Host-Umgebungen löst. Dieser technische Deep Dive untersucht, wie Plattformteams Benutzern die vollständige administrative Kontrolle über ihre Umgebungen ermöglichen und gleichzeitig eine angemessene Isolierung aufrechterhalten können – und damit die Ressourcenbeschränkungen auf Namespace-Ebene lösen, die typischerweise eine Herausforderung für mandantenfähige Architekturen darstellen. Erfahren Sie, wie vCluster Teams die Bereitstellung von clusterweiten Ressourcen wie CRDs ermöglicht und gleichzeitig die Sicherheit und Governance durch nahtlose Integration mit Sicherheitstools auf Host-Ebene gewährleistet.
Comprehensive Guide to Trivy and Trivy-Operator: From Scanning to Monitoring with Prometheus and Grafana
Securing Kubernetes environments goes beyond scanning container images. It involves visibility, automation, and continuous monitoring. Trivy and Trivy-Operator streamline vulnerability management by integrating scanning directly into your cluster operations. In this guide, we'll walk through how to use Trivy for image and configuration scanning, deploy Trivy-Operator for Kubernetes-native insights, and connect everything to Prometheus and Grafana for real-time visibility.

Building an eBPF based Open-Source observability platform
In today's world maintaining Observability and understanding what is happening inside your system in near real-time is a challenging task. The complexity arises due to the distributed nature of Cloud Infrastructure and especially Microservice based Software that has multiple components that need to communicate between each other. Keeping track of this communication and the processes involved is time consuming to track on its own.
Using the extended Berkeley Packet Filter (eBPF) technology helps transform Observability itself by allowing deep, safe, and efficient instrumentation of running systems.

Trust Nothing, Secure Everything: How to Build Zero Trust on AWS
Legacy defences just aren't cutting it anymore. According to the 2024 IBM Cost of a Data Breach Report, the global average cost of a breach has skyrocketed to $4.88 million, marking a 10% jump over last year and the highest figure on record. Even more alarming, 1 in 3 breaches involved so-called "shadow data" information that organisations didn't even know they had. The good news? By using AI and automation in security, organisations saved an average of $2.22 million per breach.

Image Scanning in Action: Securing Your Software Supply Chain
Understanding and managing vulnerabilities in modern software supply chains is more critical than ever. SBOM scanning provides transparency and helps mitigate risks effectively. In this article, we explore what SBOM scanning is, its real-world benefits, and how to integrate it into your software development lifecycle. You'll also find actionable best practices and a real-world example of its use within a microservice architecture.
