OpenBao: Wahrung der Zukunft des Open-Source-Secrets-Management
veröffentlicht am 28.07.2025 von Max Körbächer
In der komplexen Technologielandschaft von heute ist die Verwaltung von Secrets wie API-Schlüsseln, Passwörtern, Zertifikaten und anderen sensiblen Daten, zu einer der größten Herausforderungen für Unternehmen geworden. Aus diesem Grund unterstützt Liquid Reply OpenBao, ein Open-Source-System zur Verwaltung von Secrets und Verschlüsselung auf Identitätsbasis, um die Datenverwaltung im Cloud-Zeitalter zu sichern.
Was ist OpenBao?
OpenBao ist ein identitätsbasiertes System zur Verwaltung von Secrets und zur Verschlüsselung. Ein Secret ist alles, worauf Sie den Zugriff streng kontrollieren möchten, wie z. B. API-Verschlüsselungsschlüssel, Passwörter und Zertifikate. OpenBao bietet Verschlüsselungsdienste, die durch Authentifizierungs- und Autorisierungsmethoden geschützt sind.
Ursprünglich aus HashiCorp Vault hervorgegangen, hat sich OpenBao zu einem Community-gesteuerten Projekt entwickelt, das den wachsenden Bedarf an sicherer, skalierbarer und transparenter Secretsmanagement in Open-Source-Umgebungen erfüllt. Die Plattform ermöglicht es Unternehmen, alle ihre Anmeldedaten zentral zu verwalten und so die Sicherheitsrisiken zu reduzieren, die mit der Verbreitung von Anmeldedaten über mehrere Systeme und Anwendungen hinweg verbunden sind.
Der OpenBao-Ansatz: Authentifizierung, Autorisierung und Zugriff
OpenBao funktioniert nach einem einfachen, aber leistungsstarken Prinzip: OpenBao validiert und autorisiert Clients (Benutzer, Maschinen, Apps), bevor es ihnen Zugriff auf Secrets oder gespeicherte sensible Daten gewährt.
Das System arbeitet mit einem vierstufigen Workflow:
- Authentifizierung: Clients geben Informationen zur Überprüfung ihrer Identität anhand vertrauenswürdiger Authentifizierungsmethoden an.
- Validierung: OpenBao validiert Clients anhand von Drittanbieterquellen wie GitHub, LDAP oder AppRole.
- Autorisierung: Clients werden mit Sicherheitsrichtlinien abgeglichen, die festlegen, auf welche Ressourcen sie zugreifen dürfen.
- Zugriff: Nach erfolgreicher Authentifizierung und Autorisierung gibt OpenBao Tokens aus, die den Zugriff auf bestimmte Secrets und Funktionen ermöglichen.
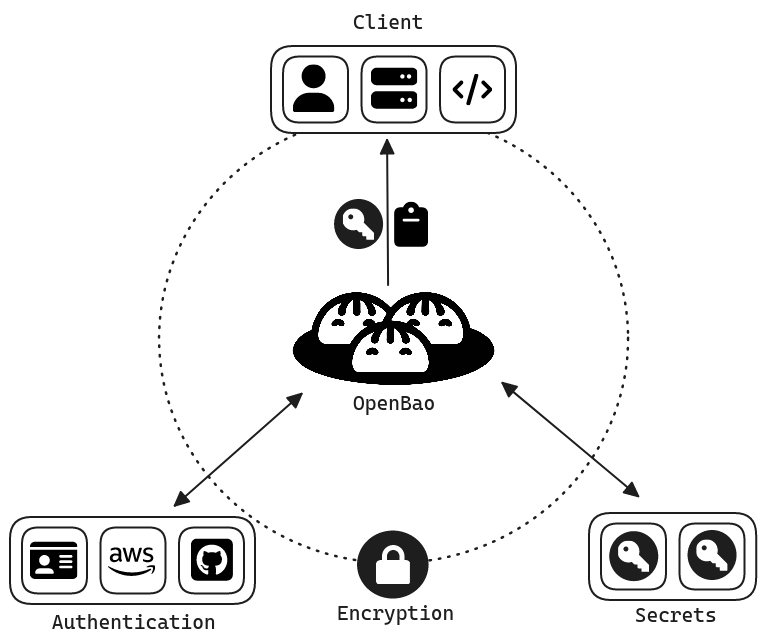
Source: https://openbao.org/docs/what-is-openbao/
Wichtige Funktionen von OpenBao
Sichere Speicherung geheimer Daten
In OpenBao können beliebige Key/Value Secrets gespeichert werden. OpenBao verschlüsselt diese Secrets, bevor sie in den persistenten Speicher geschrieben werden, sodass der Zugriff auf den Rohspeicher nicht ausreicht, um auf Ihre Secrets zuzugreifen.
Dynamische Secrets
Anstatt statische Anmeldedaten zu speichern, kann OpenBao bei Bedarf Secrets für Systeme wie Kubernetes oder SQL-Datenbanken generieren. Diese dynamischen Secrets werden automatisch widerrufen, wenn ihre Gültigkeitsdauer abläuft, wodurch das Risiko einer Offenlegung erheblich verringert wird.
Datenverschlüsselung
OpenBao bietet Verschlüsselung als Dienstleistung mit zentraler Schlüsselverwaltung, wodurch sowohl die Verschlüsselung von Daten während der Übertragung als auch im Ruhezustand vereinfacht wird. Da die Verschlüsselung innerhalb der OpenBao-Umgebung vom OpenBao-Sicherheitsteam verwaltet wird, können sich Entwickler ausschließlich auf die Anwendungslogik konzentrieren.
Umfassender Prüfpfad
Jede Aktion in OpenBao wird protokolliert, wodurch detaillierte Prüfpfade bereitgestellt werden, die für die Einhaltung von Vorschriften und die Reaktion auf Vorfälle unerlässlich sind.
Leasing- und Verlängerungssystem
Alle in OpenBao erstellten Secrets sind mit einem sogenannten Lease verbunden. Nach Ablauf eines Leases widerruft das System automatisch das Secret und schafft so einen Schutz vor potenziellen Sicherheitslücken und unbefugtem Zugriff.
Secret-Trail und Widerruf
OpenBao verfügt über eine integrierte Unterstützung für den Widerruf von Secrets und unterstützt nicht nur den Widerruf einzelner Secrets, sondern auch einer Baumstruktur von Secrets z. B. alle Secrets, die von einem bestimmten Benutzer gelesen werden, oder alle Secrets eines bestimmten Typs, wodurch eine schnelle Reaktion auf potenzielle Vorfälle ermöglicht wird.
Ein wichtiger Meilenstein: Beitritt zur OpenSSF
Als bedeutende Entwicklung für das Projekt ist OpenBao der Open Source Security Foundation (OpenSSF) als neu akzeptiertes Sandbox-Projekt beigetreten. Dieser Schritt steht für eine strategische Ausrichtung auf die breitere Open-Source-Sicherheits-Community.
„Der Beitritt zur OpenSSF ist ein Traum, der wahr geworden ist“, sagte Alex Scheel, Vorsitzender des OpenBao Technical Steering Committee. Der Übergang von LF Edge zur OpenSSF spiegelt die Entwicklung des Projekts und sein Engagement wider, den Bedürfnissen von Sicherheitsexperten und Open-Source-Betreuern gerecht zu werden.
Diese neue Partnerschaft versetzt OpenBao in die Lage, mit verschiedenen OpenSSF-Arbeitsgruppen und Interessengruppen zusammenzuarbeiten, insbesondere um die Best Practices für das Secretmanagement in Open-Source-Projekten zu stärken.
Neueste Version – Namespaces: Echte Multi-Tenancy ermöglichen
Eine der neuesten Funktionen von OpenBao ist die kürzlich angekündigte Namespaces-Funktion. Namespaces in OpenBao sind logische Partitionen innerhalb einer einzelnen OpenBao-Instanz, die als isolierte Umgebungen fungieren, in denen Teams, Organisationen oder Anwendungen unabhängig voneinander arbeiten können.
Warum Namespaces wichtig sind
Eine starke Isolierung zwischen Teams, Geschäftsbereichen oder Mandanten wird mit zunehmender Größe von Organisationen immer wichtiger, insbesondere beim Umgang mit sensiblen Daten. Namespaces ermöglichen:
- Sichere Mandantenfähigkeit: Jeder Mandant arbeitet in seinem eigenen isolierten Namespace mit streng begrenzten Berechtigungen.
- Delegierte Verwaltung: Namespace-Administratoren können ihre eigenen Richtlinien, Secret Engines und Authentifizierungsmethoden verwalten.
- Self-Service-Funktionen: Entlastet die Betreiber auf Cluster-Ebene und stärkt gleichzeitig die Teams.
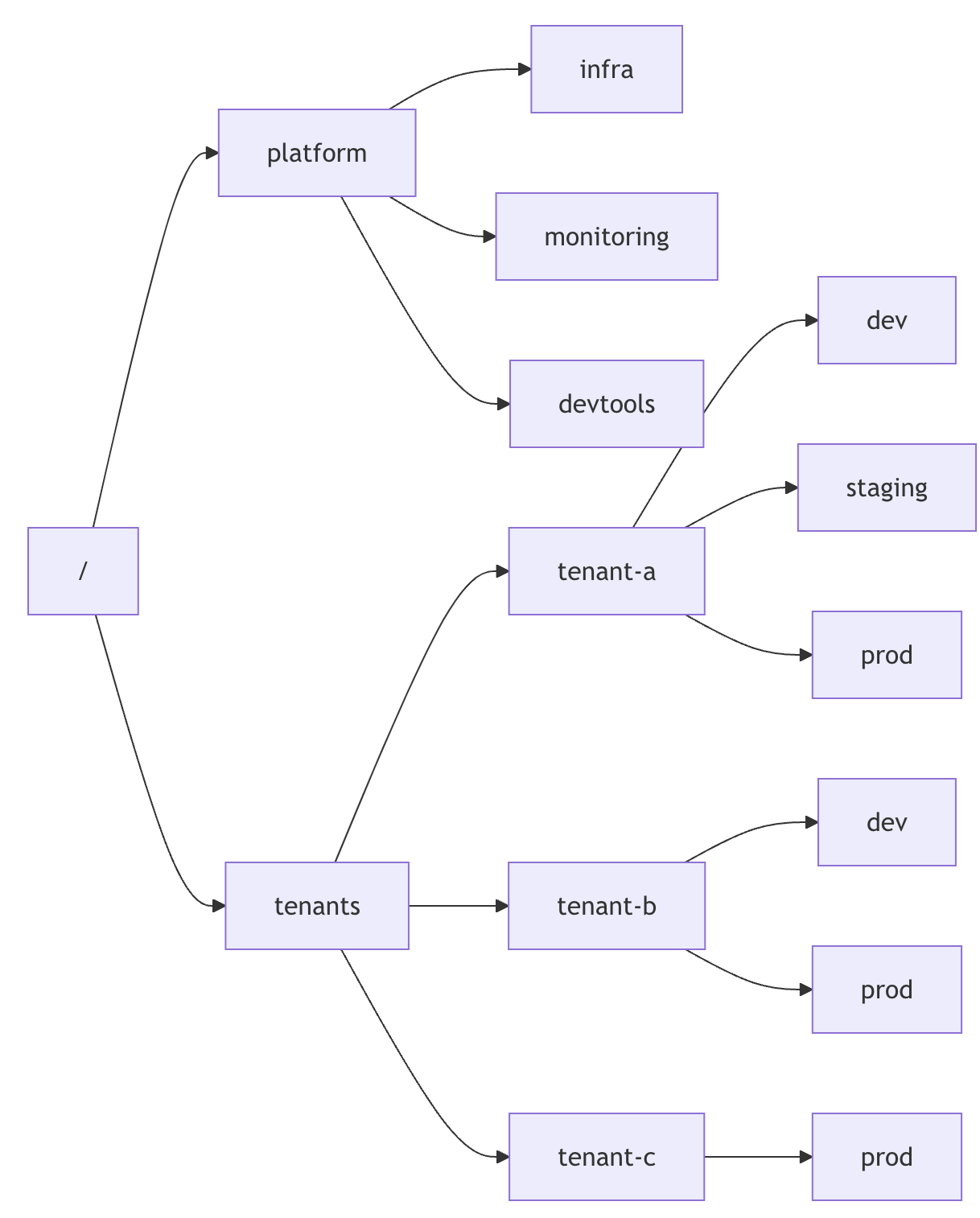
An example namespace structure to separate tenants and the platform team.
Ausblick
Der Weg zur horizontalen Skalierbarkeit
Namespaces sind der erste Schritt auf dem Weg von OpenBao zur horizontalen Skalierbarkeit. Die Vision umfasst die Unterstützung von Lazy Loading von Namespaces und Mounts, sodass Cluster Workloads mit vielen selten genutzten Ressourcen effizient bedienen können.
Der Weg zu sicherer, selbstverwalteter Multi-Tenancy
Der Sealing-Mechanismus pro Namespace bietet eine robustere und flexiblere Multi-Tenancy-Lösung, die Mandanten mehr Kontrolle über ihre Datensicherheit und -verfügbarkeit innerhalb des OpenBao-Ökosystems gibt.
Deklarative Selbstinitialisierung und Profile
Die deklarative Selbstinitialisierung ist eine neue Funktion, die durch ein flexibles Profilsystem die automatische Konfiguration beim ersten Start ermöglicht. Diese Weiterentwicklung macht manuelle Initialisierungsschritte überflüssig und ermöglicht vollständig automatisierte Bereitstellungen in modernen Infrastructure-as-a-Code-Umgebungen.
Das Profilsystem
Das Herzstück dieser Funktion ist ein neues Profilsystem, das einen Rahmen für die plattformübergreifende Kommunikation und die Orchestrierung von Anfragen bietet. Das Profilsystem verarbeitet Konfigurationsblöcke zu strukturierten API-Anfragen und unterstützt dynamische Datenquellen und die Verkettung von Anfragen für komplexe Initialisierungs-Workflows. Das System implementiert das Anfrage-/Antwortmuster, unterstützt verkettete Operationen und akzeptiert Anfrage-Handler und geparste Profilkonfigurationen. In diesem Workflow kann die Eingabe einer der folgenden Typen sein: Wert, Umgebungsvariable, Datei, Anfrage oder Antwort.
Wichtige Komponenten:
- Konfigurationsparser: Verarbeitet HCL-Konfigurationsblöcke zu ausführbaren Anfragen
- Quellcode-Generatoren: Verarbeiten dynamische Daten aus Umgebungsvariablen, Dateien und früheren Antworten
- Anfrage-Handler: Führt vorlagenbasierte Anfragen an interne APIs aus
- Verlaufsmanager: Ermöglicht den Datenfluss zwischen aufeinanderfolgenden Operationen und führt Protokolle.
Der Beitrag von Liquid Reply zu OpenBao
Als führender Experte für Cloud-native Transformationen leistet Liquid Reply einen bedeutenden Beitrag zum OpenBao-Projekt, insbesondere bei der Entwicklung der Namespaces-Funktion.
Dieser Beitrag steht im Einklang mit der Expertise von Liquid Reply in den Bereichen Plattform-Engineering und Cloud-native Entwicklung. Als Spezialisten für Multi- und Hybrid-Cloud-Lösungen wissen wir um die entscheidende Bedeutung eines robusten Secretmanagements in komplexen verteilten Systemen. Unser Engagement für OpenBao spiegelt unser Bestreben wider, Open-Source-Sicherheitstools voranzutreiben, die es Unternehmen ermöglichen, Cloud-native Transformationen sicher umzusetzen.
Unser Engagement für Open-Source-Sicherheit
Der Beitrag von Liquid Reply zu OpenBao ist Teil unseres umfassenden Engagements für die Open-Source-Community. Als Unternehmen, das Organisationen bei der Bewältigung komplexer Cloud-nativer Transformationen unterstützt, sind wir uns der entscheidenden Rolle bewusst, die eine sichere und skalierbare Secretverwaltung in modernen Infrastrukturen spielt.
Dank unserer Expertise in den Bereichen Kubernetes, Site Reliability Engineering und Operational Enablement sind wir gut positioniert, um zu Projekten wie OpenBao beizutragen, die die Grundlage für sichere Cloud-native Abläufe bilden.
Europas Versprechen
Die Entwicklung von OpenBao wird teilweise durch das IPCEI-CIS (Important Project of Common European Interest – Next Generation Cloud Infrastructures and Services) in Zusammenarbeit mit SAP finanziert und ist eine wichtige Ergänzung zu den ApeiroRA-Open-Source-Projekten, deren Ziel es ist, eine leistungsstarke Cloud-Edge-Infrastruktur auf der Grundlage europäischer Werte aufzubauen. Die ApeiroRA-Open-Source-Projekte werden unabhängig von der NeoNephos Foundation verwaltet.
Mitmachen
OpenBao steht für die Zukunft des Open-Source-Secretmanagements – sicher, skalierbar und gemeinschaftsorientiert. Ganz gleich, ob Sie Sicherheitsexperte, Entwickler oder eine Organisation sind, die ihr Secretmanagement verbessern möchte, OpenBao bietet eine robuste, transparente Alternative zu proprietären Lösungen.
Sind Sie bereit, OpenBao zu entdecken?
- Besuchen Sie das OpenBao GitHub-Repository
- Nehmen Sie an der Diskussion auf OpenSSF Slack teil
- Vernetzen Sie sich mit der Community auf Matrix
Während OpenBao seinen Weg innerhalb der OpenSSF fortsetzt, können Unternehmen weltweit von einer Lösung für das Secretmanagement profitieren, die Sicherheit, Transparenz und Zusammenarbeit in der Community in den Vordergrund stellt. Die Zukunft des Secretmanagements liegt in Open Source, und OpenBao ist dabei führend.